KYPO Cyber Range
Overview
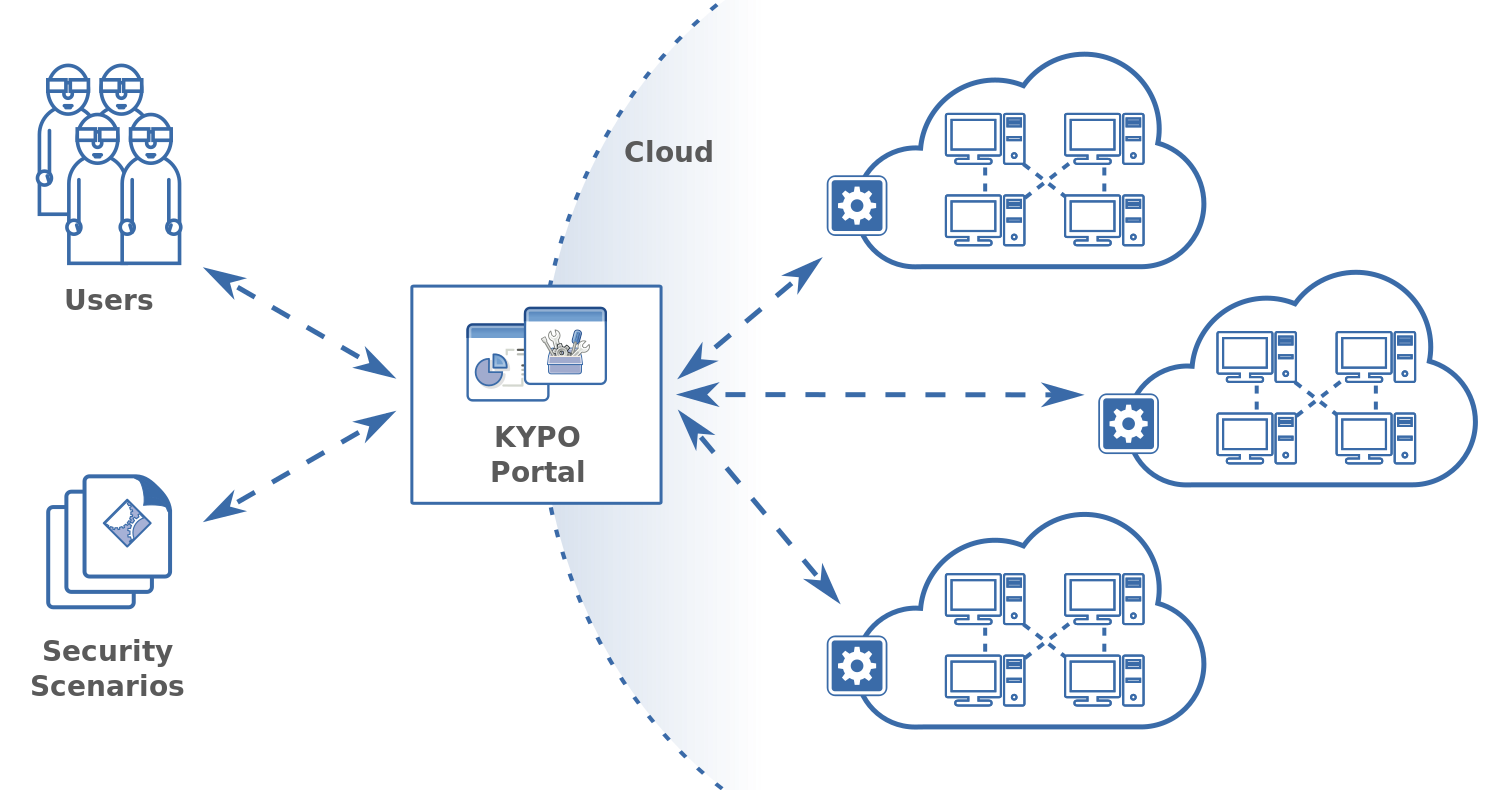
KYPO Cyber Range is a cyber exercise and research platform enabling security experts to emulate computer networks where they can perform cyber security exercises and experiments safely, without the danger of threatening the real computer infrastructure. Activities within networks are monitored by software probes which gather monitored data on the fly and store them for further ussage. Access to virtualized networks is mediated via KYPO web portal. This flexible system of adaptable user interfaces combine narrowly focused data visualizations into complex web-based interactions supporting various data exploration and collaboration strategies.
In 2016, this project obtained Award of the Ministry of Interior of the Czech Republic for the exceptional results in the field of security research.
Architecture
KYPO is designed as a multilayer application. The lower-layer includes so called sandboxes. Sandbox represents an isolated computer network where users can safely perform their tasks. Network nodes and links are build on top of a cloud managed by OpenNebula and neither users nor running applications can recognize that they do not run in real hardware and network.
Activities within a sandbox are monitored by a monitoring subsystem running in every sandbox. Acquired data are stored inside the corresponding sandbox and they are available via remote REST services.
KYPO Portal mediates access to the platform for the end users by providing them with interactive visual tools. In particular, the portal is designed to provide management services of cyber exercises, collaboration environment for an exercise participants and access to sandboxes. However, the main goal is to provide insight into the cyber security processes via specialized visualizations, interactions and GUIs. To assure high accessibility of these services for all types of end users from well-experienced security experts to unskilled students, the portal is designed as an enterprise web application where users are not bothered by the need to install anything on their device, not even browser plugins or extensions like Java or Flash.
Security scenario formalizes goals, resources and workflows required by individual use cases. They represent a basic document describing network topology and characteristics, access privileges, software running on network nodes and other necessary details. Security scenarios have the form of structured JSON files and KYPO provides several predefined templates covering various security interests and application domains like DDoS attack simulation, phishing, hacking, etc..
Use Cases
Security training: KYPO facilitates user training and exercises in many areas of computer security. In designing training sessions, project staff utilize their experience gained from participating in other training exercises (such as ENISA’s CyberEurope and NATO’s Cyber Coalition). Staff also apply their experience gained teaching at the Faculty of Informatics of Masaryk University. The main benefit of this platform for training is the high degree of user interactivity. As infrastructure can be accurately modeled, the realism of training exercises is guaranteed. User activity is monitored during training exercises and is closely evaluated to provide individualized feedback.
Cyber defence research: The KYPO Cyber Range has been designed with the needs of security research in mind. KYPO provides an environment for developing, testing, and demonstrating new methods for detecting and mitigating network attacks on critical infrastructure. Its built-in monitoring infrastructure allows it to monitor all network traffic, which can then be analyzed in detail. Thanks to scenario templates and the cloud, experiments can be repeated with precision at any time. Another useful feature is the ability to quickly transfer recorded data.
Forensic analysis and network simulation: With the KYPO platform it is possible to create virtual environments with predefined virtual machines, including mobile devices (running Android). Their network connectivity, network capacity, and allow them to connect to the internet. If predefined virtual machines do not meet your requirements, new features may be added. The platform has a built-in infrastructure for monitoring the state of the machines and the network with the help of an expandable set of variables. KYPO facilitates the forensic investigation of machines that have been compromised. In the virtual environment an attacked machine can be run repeatedly and its behavior analyzed. The KYPO’s built-in monitoring infrastructure makes machine communication data available immediately upon startup.

Selected publications
EICHLER, Zdenek, Radek OŠLEJŠEK and Dalibor TOTH. KYPO: A Tool for Collaborative Study of Cyberattacks in Safe Cloud Environment. In HCI International 2015: Human Aspects of Information Security, Privacy, and Trust. LNCS, vol. 9190. Los Angeles: Springer International Publishing, 2015. p. 190-199, 10 pp. ISBN 978-3-319-20375-1. doi:10.1007/978-3-319-20376-8_17
ČELEDA, Pavel, Jakub ČEGAN, Jan VYKOPAL and Daniel TOVARŇÁK. KYPO – A Platform for Cyber Defence Exercises. In STO-MP-MSG-133: M&S Support to Operational Tasks Including War Gaming, Logistics, Cyber Defence. Munich (Germany): NATO Science and Technology Organization, 2015. p. nestránkováno, 12 pp. ISBN 978-92-837-2020-1.
JIRSÍK, Tomáš, Martin HUSÁK, Pavel ČELEDA and Zdenek EICHLER. Cloud-based Security Research Testbed: A DDoS Use Case. In Hanan Lutfiyya and Piotr Cholda. Proceedings of the Network Operations and Management Symposium (NOMS 2014). Krakow, Poland: IEEE Xplore Digital Library, 2014. p. 1-2, 2 pp. ISBN 978-1-4799-0912-4. doi:10.1109/NOMS.2014.6838272.



